Kaspersky malware probers have uncovered a new ‘operating system’-like platform they was developed and used by the National Security Agency (NSA) in its Equation spying arsenal.
The EquationDrug or Equestre platform is used to deploy 116 modules to target computers that can siphon data and spy on victims.
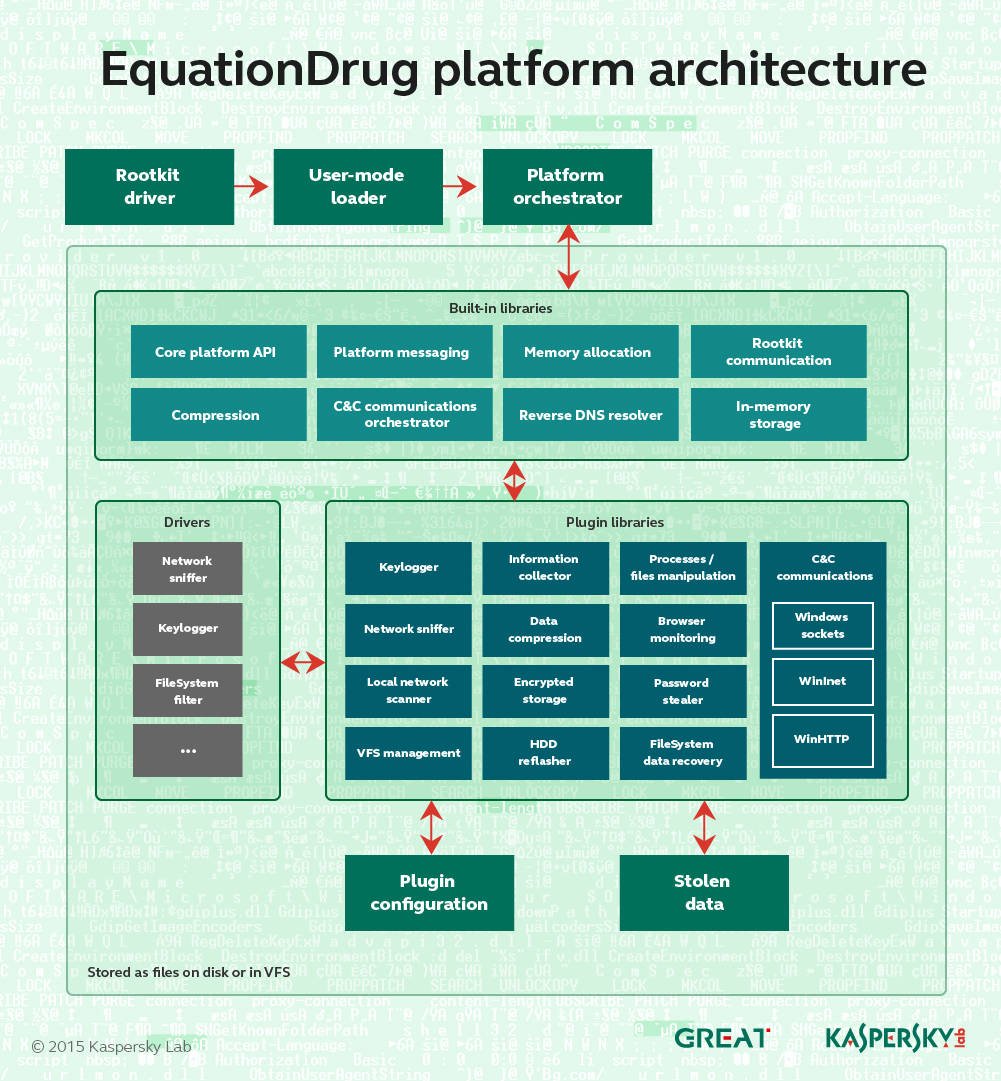
“It’s important to note that EquationDrug is not just a trojan, but a full espionage platform, which includes a framework for conducting cyberespionage activities by deploying specific modules on the machines of selected victims,” Kaspersky researchers say in a report.
“Other threat actors known to use such sophisticated platforms include Regin and Epic Turla.
“The architecture of the whole framework resembles a mini-operating system with kernel-mode and user-mode components carefully interacting with each other via a custom message-passing interface.”
The platform is part of the NSA’s possibly ongoing campaign to infect hard disk firmware. It replaces the older EquationLaser and is itself superseded by the GrayFish platform.
Kaspersky says the newly-identified wares are as “sophisticated as a space station” thanks to the sheer number of included espionage tools.
Extra modules can be added through a custom encrypted file system containing dozens of executables that together baffle most security bods.
Most of the unique identifiers and codenames tied to modules is encrypted and obfuscated. Some modules capabilities can be determined with unique identification numbers. Others are dependent on other plugins to function.
Each plugin has a unique ID and version number that defines a set of functions it can provide. Some of the plugins depend on others and might not work unless dependencies are resolved.
Kaspersky bods have found 30 of the 116 modules estimated to exist.
“The plugins we discovered probably represent just a fraction of the attackers’ potential,” the researchers say.
Executable timestamps reveal NSA developers likely work hardest on the platform on Tuesdays to Fridays, perhaps having late starts to Monday.
Modules detected in the tool include code for:
- Network traffic interception for stealing or re-routing
- Reverse DNS resolution (DNS PTR records)
- Computer management
- Start/stop processes
- Load drivers and libraries
- Manage files and directories
- System information gathering
- OS version detection
- Computer name detection
- User name detection
- Locale detection
- Keyboard layout detection
- Timezone detection
- Process list
- Browsing network resources and enumerating and accessing shares
- WMI information gathering
- Collection of cached passwords
- Enumeration of processes and other system objects
- Monitoring LIVE user activity in web browsers
- Low-level NTFS filesystem access based on the popular Sleuthkit framework
- Monitoring removable storage drives
- Passive network backdoor (runs Equation shellcode from raw traffic)
- HDD and SSD firmware manipulation
- Keylogging and clipboard monitoring
- Browser history, cached passwords and form auto-fill data collection.
Tag: Russia
New Anti-Corruption Social Network In Russia Requires Numerous Personal Details To Join: What Could Possibly Go Wrong?
As the murder of the opposition politician Boris Nemtsov last week reminds us, the political situation in Russia is not just difficult, but extremely dangerous. Presumably hoping that technology might offer a relative safe way to cope with this situation, a Russian NGO has announced that it will be launching a nationwide social network dedicated to fighting bribery and corruption. You might expect that anonymity would be a crucial aspect, given the risks faced by those who choose to join. And yet, as this RT article explains, that’s not the case (via @prfnv):
the new project will have one major difference from existing social networks — a complete lack of anonymity. Membership will only be granted by invitation from existing members, and even when this condition is met, the institute that launches the project promises to open accounts only after verifying the identity of potential members in real life.
The users will have to provide a lot of details about themselves — from name and date of birth, to place of work, e-mail and phone numbers. The people launching the project say that this is a necessary measure to prevent attempted slander, which they see as the main danger threatening their network.
Let’s blame Iran (again)
US director of National Intelligence James Clapper has accused Iran of orchestrating a 2014 hack of the Las Vegas Sands casino. The attack crippled the magnificent cultural institution’s IT infrastructure.
Clapper told a US Senate Armed Services Committee Thursday (US time) that the hack of the US$14 billion casino was the handiwork of Iran rather than ordinary hacking groups, Bloomberg reports.
“While both of these nations (Iran and North Korea) have lesser technical capabilities in comparison to Russia and China, these destructive attacks demonstrate that Iran and North Korea are motivated and unpredictable cyber-actors,” Clapper says.
The attacks brought down the casino’s IT systems including email but not the most valuable components of the organisation.
NSA Director: If I Say ‘Legal Framework’ Enough, Will It Convince You Security People To Shut Up About Our Plan To Backdoor Encryption?
Admiral Mike Rogers, the NSA Director, has barely been on the job for a year, and so far he’d mostly avoided making the same kinds of absolutely ridiculous statements that his predecessor General Keith Alexander was known for. Rogers had, at the very least, appeared slightly more thoughtful in his discussions about the surveillance state and his own role in it. However, Rogers ran into a bit of trouble at New America’s big cybersecurity event on Monday — in that there were actual cybersecurity folks in the audience and they weren’t accepting any of Rogers’ bullshit answers. The most notable exchange was clearly between Rogers and Alex Stamos, Yahoo’s chief security officer, and a well known privacy/cybersecurity advocate.
Alex Stamos (AS): “Thank you, Admiral. My name is Alex Stamos, I’m the CISO for Yahoo!. … So it sounds like you agree with Director Comey that we should be building defects into the encryption in our products so that the US government can decrypt…
Mike Rogers (MR): That would be your characterization. [laughing]
AS: No, I think Bruce Schneier and Ed Felton and all of the best public cryptographers in the world would agree that you can’t really build backdoors in crypto. That it’s like drilling a hole in the windshield.
MR: I’ve got a lot of world-class cryptographers at the National Security Agency.
AS: I’ve talked to some of those folks and some of them agree too, but…
MR: Oh, we agree that we don’t accept each others’ premise. [laughing]
AS: We’ll agree to disagree on that. So, if we’re going to build defects/backdoors or golden master keys for the US government, do you believe we should do so — we have about 1.3 billion users around the world — should we do for the Chinese government, the Russian government, the Saudi Arabian government, the Israeli government, the French government? Which of those countries should we give backdoors to?
MR: So, I’m not gonna… I mean, the way you framed the question isn’t designed to elicit a response.
AS: Well, do you believe we should build backdoors for other countries?
MR: My position is — hey look, I think that we’re lying that this isn’t technically feasible. Now, it needs to be done within a framework. I’m the first to acknowledge that. You don’t want the FBI and you don’t want the NSA unilaterally deciding, so, what are we going to access and what are we not going to access? That shouldn’t be for us. I just believe that this is achievable. We’ll have to work our way through it. And I’m the first to acknowledge there are international implications. I think we can work our way through this.
AS: So you do believe then, that we should build those for other countries if they pass laws?
MR: I think we can work our way through this.
AS: I’m sure the Chinese and Russians are going to have the same opinion.
MR: I said I think we can work through this.
AS: Okay, nice to meet you. Thanks.
[laughter]
MR: Thank you for asking the question. I mean, there are going to be some areas where we’re going to have different perspectives. That doesn’t bother me at all. One of the reasons why, quite frankly, I believe in doing things like this is that when I do that, I say, “Look, there are no restrictions on questions. You can ask me anything.” Because we have got to be willing as a nation to have a dialogue. This simplistic characterization of one-side-is-good and one-side-is-bad is a terrible place for us to be as a nation. We have got to come to grips with some really hard, fundamental questions. I’m watching risk and threat do this, while trust has done that. No matter what your view on the issue is, or issues, my only counter would be that that’s a terrible place for us to be as a country. We’ve got to figure out how we’re going to change that.
[Moderator Jim Sciutto]: For the less technologically knowledgeable, which would describe only me in this room today, just so we’re clear: You’re saying it’s your position that in encryption programs, there should be a backdoor to allow, within a legal framework approved by the Congress or some civilian body, the ability to go in a backdoor?
MR: So “backdoor” is not the context I would use. When I hear the phrase “backdoor,” I think, “well, this is kind of shady. Why would you want to go in the backdoor? It would be very public.” Again, my view is: We can create a legal framework for how we do this. It isn’t something we have to hide, per se. You don’t want us unilaterally making that decision, but I think we can do this.
Russia Reaches The Censorship Endgame: Banning VPNs, Tor And Web Proxies
Speaking at Infoforum-2015, Russian MP Leonid Levin, who is deputy head of the Duma Committee on information politics, indicated that access to anonymization and circumvention tools such as TOR, VPNs and even web proxies, needs to be restricted.
Researchers Find ‘Astonishing’ Malware Linked to NSA Spying
Security researchers have uncovered highly sophisticated malware that is linked to a secret National Security Agency hacking operation exposed by The Intercept last year.
Russian security firm Kaspersky published a report Monday documenting the malware, which it said had been used to infect thousands of computer systems and steal data in 30 countries around the world. Among the targets were a series of unnamed governments, telecom, energy, and aerospace companies, as well as Islamic scholars, and media organizations.
Kaspersky did not name the NSA as the author of the malware. However, Reuters reported later on Monday that the agency had created the technology, citing anonymous former U.S. intelligence officials.
Kaspersky’s researchers noted that the newly found malware is similar to Stuxnet, a covert tool reportedly created by the U.S. government to sabotage Iranian nuclear systems. The researchers also identified a series of codenames that they found contained within the samples of malware, including STRAIGHTACID, STRAITSHOOTER, and GROK.
Notably, GROK, which Kaspersky said is a piece of malware used to secretly log keystrokes, is tied to secret NSA hacking tactics described in documents from whistleblower Edward Snowden. Last year, The Intercept revealed that the NSA was using a tool called GROK to log keystrokes as part of a toolkit it uses to hack computers and collect data.
The other codenames identified by Kaspersky on Tuesday—such as STRAIGHTACID, STRAITSHOOTER—are strikingly similar to known NSA hacking operations. Leaked NSA documents have revealed that the agency uses hacking tools known as STRAIGHTBIZARRE and FOXACID to break into computers and grab data.
According to Kaspersky, the malware found in the latest discovery is the most advanced ever found and represents an “astonishing technical accomplishment.” It hides deep within an infected computer and can stay on the machine even after attempts to wipe or reformat the hard drive. The security firm has dubbed different variants of the malware EquationLaser, EquationDrug and GrayFish, and they are calling its creators the “Equation Group,” because of the way the spy technology attempts to hide itself in an infected computer using complex encryption.