Yesterday we talked about the ridiculousness of President Obama’s new cybersecurity executive order, in which he declares a national emergency around “malicious cyber-enabled activities” and enables his own government to do mean things to anyone they think is responsible for cyber badness (that his own NSA is the primary instigator of serious cyberattacks gets left ignored, of course). One of the points we made is that the definitions in the executive agreement were really vague, meaning that it’s likely that they could be abused in all sorts of ways that we wouldn’t normally think of as malicious hacking.
Helpfully, the ever vigilant Marcey Wheeler has provided some examples of how the vague language can and likely will be twisted:
The EO targets not just the hackers themselves, but also those who benefit from or materially support hacks. The targeting of those who are “responsible for or complicit in … the receipt or use for commercial or competitive advantage … by a commercial entity, outside the United States of trade secrets misappropriated through cyber-enabled means, … where the misappropriation of such trade secrets is reasonably likely to result in, or has materially contributed to, a significant threat to the national security, foreign policy, or economic health or financial stability of the United States” could be used to target journalism abroad. Does WikiLeaks’ publication of secret Trans-Pacific Partnership negotiations qualify? Does Guardian’s publication of contractors’ involvement in NSA hacking?
And, that’s not all. How about encryption providers? Not too hard to see how they might qualify:
And the EO creates a “material support” category similar to the one that, in the terrorism context, has been ripe for abuse. Its targets include those who have “provided … material, or technological support for, or goods or services in support of” such significant hacks. Does that include encryption providers? Does it include other privacy protections?And the EO creates a “material support” category similar to the one that, in the terrorism context, has been ripe for abuse. Its targets include those who have “provided … material, or technological support for, or goods or services in support of” such significant hacks. Does that include encryption providers? Does it include other privacy protections?
We’ve already seen some — including government officials — argue that Twitter could be deemed to be providing “material support” to ISIS if it didn’t take down Twitter accounts that support ISIS. Twitter wouldn’t directly qualify under this executive order (which targets non-US actors), but it shows you how easy it is to stretch this kind of thinking in dangerous ways.
Making sure the technology we use every day is secure is important. But vaguely worded executive orders and an over-hyped “national emergency” isn’t the solution. Instead, it’s likely to be abused in serious ways that harm our freedoms.
Tag: NSA
Britain Used Spy Team to Shape Latin American Public Opinion on Falklands
Faced with mounting international pressure over the Falkland Islands territorial dispute, the British government enlisted its spy service, including a highly secretive unit known for using “dirty tricks,” to covertly launch offensive cyberoperations to prevent Argentina from taking the islands.
A shadowy unit of the British spy agency Government Communications Headquarters (GCHQ) had been preparing a bold, covert plan called “Operation QUITO” since at least 2009. Documents provided to The Intercept by National Security Agency whistleblower Edward Snowden, published in partnership with Argentine news site Todo Notícias, refer to the mission as a “long-running, large scale, pioneering effects operation.”
At the heart of this operation was the Joint Threat Research and Intelligence Group, known by the acronym JTRIG, a secretive unit that has been involved in spreading misinformation.
The British government, which has continuously administered the Falkland Islands — also known as the Malvinas — since 1833, has rejected Argentine and international calls to open negotiations on territorial sovereignty. Worried that Argentina, emboldened by international opinion, may attempt to retake the islands diplomatically or militarily, JTRIG and other GCHQ divisions were tasked “to support FCO’s [Foreign and Commonwealth Office’s] goals relating to Argentina and the Falkland Islands.” A subsequent document suggests the main FCO goal was to “[prevent] Argentina from taking over the Falkland Islands” and that new offensive cyberoperations were underway in 2011 to further that end.
Tensions between the two nations, which fought a war over the small archipelago in the South Atlantic Ocean in 1982, reached a boil in 2010 with the British discovery of large, offshore oil and gas reserves potentially worth billions of dollars.
The British government frames the issue as one of residents’ self-determination. Prime Minister David Cameron maintains that the islands will remain British as long as that was the will of their inhabitants, “full stop, end of story.”
Argentine President Cristina Kirchner, known for her provocative, left-leaning foreign policy since taking office in 2007, rallied regional and international leaders to pass resolutions in international bodies supportive of Argentina’s claim to the islands and stand against what she called the U.K.’s “downright colonialism.”
Even the United States, Britain’s closest ally, declined to support the U.K. position, instead offering to mediate a resolution between the two sides in 2010. Prime Minister Cameron rejected the proposal, calling it “disappointing.”
GCHQ’s efforts on Argentina and the Falklands between 2008 and 2011, the time period the documents cover, were broad and not limited solely to JTRIG. Surveillance of Argentine “military and Leadership” communications on various platforms was a “high priority” task. Despite the Obama administration’s unwillingness to publicly back their ally, NSA assistance was ongoing as of 2010. According to an NSA “Extended Enterprise Report” dated June 2008, based on NSA officials’ meetings with GCHQ representatives, Argentina was “GCHQ’s primary interest in the region.”
Dangerously Underpowered NSA Begging Legislators For Permission To Go To Cyberwar
NSA director Mike Rogers testified in front of a Senate committee this week, lamenting that the poor ol’ NSA just doesn’t have the “cyber-offensive” capabilities (read: the ability to hack people) it needs to adequately defend the US. How cyber-attacking countries will help cyber-defense is anybody’s guess, but the idea that the NSA is somehow hamstrung is absurd.
Yes, we (or rather, our representatives) are expected to believe the NSA is just barely getting by when it comes to cyber-capabilities. Somehow, backdoors in phone SIM cards, backdoors in networking hardware, backdoors in hard drives, compromised encryption standards, collection points on internet backbones, the cooperation of national security agencies around the world, stealth deployment of malicious spyware, the phone records of pretty much every American, access to major tech company data centers, an arsenal of purchased software and hardware exploits, various odds and ends yet to be disclosed and the full support of the last two administrations just isn’t enough. Now, it wants the blessing of lawmakers to do even more than it already does. Which is quite a bit, actually.
The NSA runs sophisticated hacking operations all over the world. A Washington Post report showed that the NSA carried out 231 “offensive” operations in 2011 – and that number has surely grown since then. That report also revealed that the NSA runs a $652m project that has infected tens of thousands of computers with malware.
That was four years ago — a lifetime when it comes to an agency with the capabilities the NSA possesses. Anyone who believes the current numbers are lower is probably lobbying increased power. And they don’t believe it. They’d just act like they do.
US Threatened Germany Over Snowden, Vice Chancellor Says
German Vice Chancellor Sigmar Gabriel said this week in Homburg that the U.S. government threatened to cease sharing intelligence with Germany if Berlin offered asylum to NSA whistleblower Edward Snowden or otherwise arranged for him to travel to that country. “They told us they would stop notifying us of plots and other intelligence matters,” Gabriel said.
The vice chancellor delivered a speech in which he praised the journalists who worked on the Snowden archive, and then lamented the fact that Snowden was forced to seek refuge in “Vladimir Putin’s autocratic Russia” because no other nation was willing and able to protect him from threats of imprisonment by the U.S. government (I was present at the event to receive an award). That prompted an audience member to interrupt his speech and yell out: “Why don’t you bring him to Germany, then?”
There has been a sustained debate in Germany over whether to grant asylum to Snowden, and a major controversy arose last year when a Parliamentary Committee investigating NSA spying divided as to whether to bring Snowden to testify in person, and then narrowly refused at the behest of the Merkel government. In response to the audience interruption, Gabriel claimed that Germany would be legally obligated to extradite Snowden to the U.S. if he were on German soil.
Afterward, however, when I pressed the vice chancellor (who is also head of the Social Democratic Party, as well as the country’s economy and energy minister) as to why the German government could not and would not offer Snowden asylum — which, under international law, negates the asylee’s status as a fugitive — he told me that the U.S. government had aggressively threatened the Germans that if they did so, they would be “cut off” from all intelligence sharing. That would mean, if the threat were carried out, that the Americans would literally allow the German population to remain vulnerable to a brewing attack discovered by the Americans by withholding that information from their government.
Cisco posts kit to empty houses to dodge NSA chop shops
Cisco will ship boxes to vacant addresses in a bid to foil the NSA, security chief John Stewart says.
The dead drop shipments help to foil a Snowden-revealed operation whereby the NSA would intercept networking kit and install backdoors before boxen reached customers.
The interception campaign was revealed last May.
Speaking at a Cisco Live press panel in Melbourne today, Stewart says the Borg will ship to fake identities for its most sensitive customers, in the hope that the NSA’s interceptions are targeted.
“We ship [boxes] to an address that’s has nothing to do with the customer, and then you have no idea who ultimately it is going to,” Stewart says.
“When customers are truly worried … it causes other issues to make [interception] more difficult in that [agencies] don’t quite know where that router is going so its very hard to target – you’d have to target all of them.
There is always going to be inherent risk.”
Stewart says some customers drive up to a distributor and pick up hardware at the door.
He says nothing could guarantee protection against the NSA, however. “If you had a machine in an airtight area … I stop the controls by which I mitigate risk when I ship it,” he says, adding that hardware technologies can make malicious tampering “incredibly hard”.
Cisco has poked around is routers for possible spy chips, but to date has not found anything because it necessarily does not know what NSA taps may look like, according to Stewart.
After the hacking campaign Borg boss John Chambers wrote a letter to US President Barack Obama saying the spying would undermine the global tech industry.
New Zealand Used NSA System to Target Officials, Anti-Corruption Campaigner
New Zealand’s eavesdropping agency used an Internet mass surveillance system to target government officials and an anti-corruption campaigner on a neighboring Pacific island, according to a top-secret document.
Analysts from Government Communications Security Bureau, or GCSB, programmed the Internet spy system XKEYSCORE to intercept documents authored by the closest aides and confidants of the prime minister on the tiny Solomon Islands. The agency also entered keywords into the system so that it would intercept documents containing references to the Solomons’ leading anti-corruption activist, who is known for publishing government leaks on his website.
XKEYSCORE is run by the National Security Agency, and is used to analyze billions of emails, Internet browsing sessions and online chats that are collected from some 150 different locations worldwide. GCSB has gained access to XKEYSCORE because New Zealand is a member of the Five Eyes surveillance alliance alongside the United States, the United Kingdom, Canada and Australia.
A number of GCSB’s XKEYSCORE targets are disclosed in a top-secret document that was obtained by The Intercept and New Zealand newspaper the Herald on Sunday. The document raises questions about the scope of the surveillance and offers an unprecedented insight into specific people monitored by New Zealand’s most secretive agency.
The targets list, dated from January 2013, was authored by a GCSB analyst. It is contained in a so-called “fingerprint,” a combination of keywords used to extract particular information from the vast quantities of intercepted data swept up by XKEYSCORE. None of the individuals named on the list appear to have any association with terrorism.
Most of the targets, in fact, had a prominent role in the Solomon Islands government. Their roles around the time of January 2013 suggest GCSB was interested in collecting information sent among the prime minister’s inner circle. The targets included: Barnabas Anga, the permanent secretary of the Ministry of Foreign Affairs and External Trade; Robert Iroga, chief of staff to the prime minister; Dr Philip Tagini, special secretary to the prime minister; Fiona Indu, senior foreign affairs official; James Remobatu, cabinet secretary; and Rose Qurusu, a Solomon Islands public servant.
The seventh person caught up in the GCSB’s surveillance sweep is the leading anti-corruption campaigner in the Solomon Islands, Benjamin Afuga. For several years he has run a popular Facebook group that exposes corruption, often publishing leaked information and documents from government whistleblowers. His organization, Forum Solomon Islands International, has an office next door to Transparency International in Honiara, the capital city of the Solomon Islands. GCSB analysts programmed XKEYSCORE so that it would intercept documents sent over the Internet containing the words “Forum Solomon Islands,” “FSII,” and “Benjamin Afuga.”
Ron Wyden: ‘Plenty’ Of Domestic Surveillance Programs Still Unexposed
In a few months, we’ll be marking the second anniversary of the first Snowden leak. The outraged responses of citizens and politicians around the world to these revelations has resulted in approximately nothing in those 24 months. There have been bright spots here and there — where governments and their intelligence agencies were painted into corners by multiple leaks and forced to respond — but overall, the supposed debate on the balance between security and privacy has been largely ignored by those on Team National Security.
Here in the US, multiple surveillance reforms were promised. So far, very little has been put into practice. The NSA may be forced to seek court approval for searches of its bulk phone metadata, but otherwise the program rolls on unimpaired and slightly rebranded (from Section 215 to Section 501).
Senator Ron Wyden — one of the few members of our nation’s intelligence oversight committees actively performing any oversight — isn’t happy with the lack of progress. In an interview with Buzzfeed’s John Stanton, Wyden points out that not only has there been little movement forward in terms of surveillance reform, there actually may have been a few steps backward.
Wyden bluntly warned that even after the NSA scandal that started with Edward Snowden’s disclosures, the Obama administration has continued programs to monitor the activities of American citizens in ways that the public is unaware of and that could be giving government officials intimate details of citizens’ lives.
Asked if intelligence agencies have domestic surveillance programs of which the public is still unaware, Wyden said simply, “Yeah, there’s plenty of stuff.
Angry Austrian could turn Europe against the US – thanks to data
In a David versus Goliath battle, an Austrian law student may topple the biggest EU-US data sharing deal when he gets his day in court in a couple of weeks’ time.
Max Schrems, who set up the Europe v Facebook group, alleges that Facebook violated the so-called safe harbour agreement which protects EU citizens’ privacy by transferring personal user data to the US National Security Agency (NSA).
The European Court of Justice (ECJ) will hear details of the case on 24 March.
Schrems first appealed to the Irish Data Protection Commissioner to investigate his claims. He was refused on the grounds that Facebook was signed up to the safe harbour agreement and so could transfer data to the US with impunity.
Under European data protection law, companies can only transfer consumer data out of the EU to countries where there is an “adequate” level of privacy protection. As the US does not meet this adequacy standard, the European Commission and the US authorities came up with a workaround and, in 2000, set up the voluntary safe harbour framework whereby companies promise to protect European citizens’ data.
These promises are enforced by the US Federal Trade Commission – but since the Snowden revelations, there has been doubt these promises are worth the paper they’re written on.
Kaspersky claims to have found NSA’s ‘space station malware’
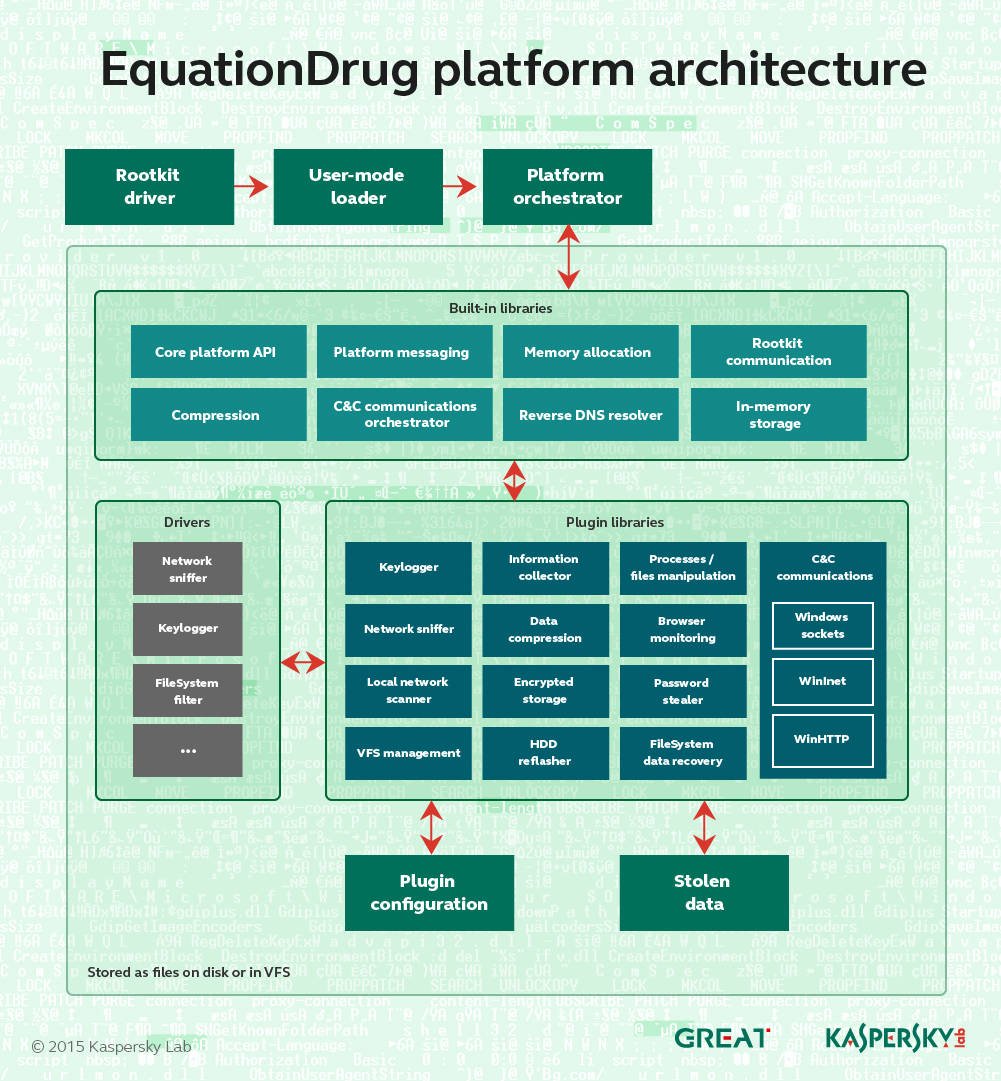
Kaspersky malware probers have uncovered a new ‘operating system’-like platform they was developed and used by the National Security Agency (NSA) in its Equation spying arsenal.
The EquationDrug or Equestre platform is used to deploy 116 modules to target computers that can siphon data and spy on victims.
“It’s important to note that EquationDrug is not just a trojan, but a full espionage platform, which includes a framework for conducting cyberespionage activities by deploying specific modules on the machines of selected victims,” Kaspersky researchers say in a report.
“Other threat actors known to use such sophisticated platforms include Regin and Epic Turla.
“The architecture of the whole framework resembles a mini-operating system with kernel-mode and user-mode components carefully interacting with each other via a custom message-passing interface.”
The platform is part of the NSA’s possibly ongoing campaign to infect hard disk firmware. It replaces the older EquationLaser and is itself superseded by the GrayFish platform.
Kaspersky says the newly-identified wares are as “sophisticated as a space station” thanks to the sheer number of included espionage tools.
Extra modules can be added through a custom encrypted file system containing dozens of executables that together baffle most security bods.
Most of the unique identifiers and codenames tied to modules is encrypted and obfuscated. Some modules capabilities can be determined with unique identification numbers. Others are dependent on other plugins to function.
Each plugin has a unique ID and version number that defines a set of functions it can provide. Some of the plugins depend on others and might not work unless dependencies are resolved.
Kaspersky bods have found 30 of the 116 modules estimated to exist.
“The plugins we discovered probably represent just a fraction of the attackers’ potential,” the researchers say.
Executable timestamps reveal NSA developers likely work hardest on the platform on Tuesdays to Fridays, perhaps having late starts to Monday.
Modules detected in the tool include code for:
- Network traffic interception for stealing or re-routing
- Reverse DNS resolution (DNS PTR records)
- Computer management
- Start/stop processes
- Load drivers and libraries
- Manage files and directories
- System information gathering
- OS version detection
- Computer name detection
- User name detection
- Locale detection
- Keyboard layout detection
- Timezone detection
- Process list
- Browsing network resources and enumerating and accessing shares
- WMI information gathering
- Collection of cached passwords
- Enumeration of processes and other system objects
- Monitoring LIVE user activity in web browsers
- Low-level NTFS filesystem access based on the popular Sleuthkit framework
- Monitoring removable storage drives
- Passive network backdoor (runs Equation shellcode from raw traffic)
- HDD and SSD firmware manipulation
- Keylogging and clipboard monitoring
- Browser history, cached passwords and form auto-fill data collection.
AT&T’s Cozy NSA Ties Brought Up In Attempt To Scuttle DirecTV Merger
Before there was Edward Snowden, there was of course the notably less celebrated Mark Klein. As most of you probably recall, Klein, a 22-year AT&T employee, became a whistleblower after hehighlighted how AT&T was effectively using fiber splits to give the NSA duplicate access to every shred of data that touched AT&T’s network. Of course, once it was discovered that AT&T was breaking the law, the government decided to just change the law, ignore Klein’s testimony, and give all phone companies retroactive immunity. It really wasn’t until Snowden that the majority of the tech press took Klein’s warnings seriously.
AT&T’s been loyally “patriotic” ever since, often giving the government advice on how to skirt the lawor at times even acting as intelligence analysts. Business repercussions for AT&T have been minimal at best; in fact, you’ll recall that Qwest (now CenturyLink) claimed repeatedly that government cooperation was rewarded with lucrative contracts, while refusal to participate in government programs was punished. In fact, the only snag AT&T’s seen in the years since was to have its European expansion plans thwarted, purportedly by regulators uncomfortable with the carrier’s cozy NSA ties (AT&T instead simply expanded into Mexico).
Fast forward a few years and The Hill is now claiming that AT&T’s relationship with the NSA could harm the company’s $48 billion attempt to acquire DirecTV. This claim is apparently based on the fact that a coalition of AT&T business partners, called the Minority Cellular Partners Coalition, is warning the FCC in a letter that AT&T’s enthusiastic voluntary cooperation with the NSA shows the company’s total disregard for consumer privacy.
“(Despite immunity) the Commission is still obliged to execute and enforce the provisions of § 229 of the Act, see 47 U.S.C. § 151, and it is still empowered to conduct an investigation to insure that AT&T complies with the requirements of CALEA. See id. § 229(c). And the Commission is obliged to determine whether AT&T is qualified to obtain DIRECTV’s licenses in light of its egregious violations of CALEA. This is particularly true given AT&T’s continued and ongoing pattern of misconduct. Accordingly, the Commission should investigate AT&T’s complicity in the PSP to determine whether AT&T engaged in unlawful conduct that abridged the privacy interests of telecommunications consumers on a vast scale and, if so, whether AT&T is qualified to obtain DIRECTV’s licenses.”
Of course, that’s simply not happening. While the NSA cooperation can be used as a broader example of AT&T’s character (like the repeatedly nonsensical claims the company makes when it wants a merger approved, or how AT&T tries to charge its broadband customers extra for no deep packet inspection), it’s incredibly unlikely that the same government that granted AT&T’s immunity will turn around and sign off on using AT&T’s behavior to squash a merger. If the merger is blocked, it will be due to more practical considerations — like the fact that DirecTV is a direct competitor to AT&T and eliminating them would lessen competition in the pay TV space. When it comes to AT&T’s relationship with the NSA, it’s pretty clear by now that these particular chickens may never come home to roost.