Just as the Bush administration and the U.S. media re-labelled “torture” with the Orwellian euphemism “enhanced interrogation techniques” to make it more palatable, the governments and media of the Five Eyes surveillance alliance are now attempting to re-brand “mass surveillance” as “bulk collection” in order to make it less menacing (and less illegal). In the past several weeks, this is the clearly coordinated theme that has arisen in the U.S., U.K., Canada, Australia and New Zealand as the last defense against the Snowden revelations, as those governments seek to further enhance their surveillance and detention powers under the guise of terrorism.
This manipulative language distortion can be seen perfectly in yesterday’s white-washing report of GCHQ mass surveillance from the servile rubber-stamp calling itself “The Intelligence and Security Committee of the UK Parliament (ISC)”(see this great Guardian editorial this morning on what a “slumbering” joke that “oversight” body is). As Committee Member MP Hazel Blears explained yesterday (photo above), the Parliamentary Committee officially invoked this euphemism to justify the collection of billions of electronic communications events every day.
The Committee actually acknowledged for the first time (which Snowden documents long ago proved) that GCHQ maintains what it calls “Bulk Personal Datasets” that contain “millions of records,” and even said about pro-privacy witnesses who testified before it: “we recognise their concerns as to the intrusive nature of bulk collection.” That is the very definition of “mass surveillance,” yet the Committee simply re-labelled it “bulk collection,” purported to distinguish it from “mass surveillance,” and thus insist that it was all perfectly legal.
Category: Spying
Angry Austrian could turn Europe against the US – thanks to data
In a David versus Goliath battle, an Austrian law student may topple the biggest EU-US data sharing deal when he gets his day in court in a couple of weeks’ time.
Max Schrems, who set up the Europe v Facebook group, alleges that Facebook violated the so-called safe harbour agreement which protects EU citizens’ privacy by transferring personal user data to the US National Security Agency (NSA).
The European Court of Justice (ECJ) will hear details of the case on 24 March.
Schrems first appealed to the Irish Data Protection Commissioner to investigate his claims. He was refused on the grounds that Facebook was signed up to the safe harbour agreement and so could transfer data to the US with impunity.
Under European data protection law, companies can only transfer consumer data out of the EU to countries where there is an “adequate” level of privacy protection. As the US does not meet this adequacy standard, the European Commission and the US authorities came up with a workaround and, in 2000, set up the voluntary safe harbour framework whereby companies promise to protect European citizens’ data.
These promises are enforced by the US Federal Trade Commission – but since the Snowden revelations, there has been doubt these promises are worth the paper they’re written on.
Dutch Court Sets Aside National Data Retention Law
Back in January, we wrote about a legal challenge to the Netherlands’ data retention law by a group of civil rights organizations. This was because the Dutch government had decided to ignore the important ruling by Europe’s highest court, the Court of Justice of the EU (CJEU), that blanket data retention was “invalid.” Now, a court in The Hague has ruled the government was wrong to do so:
Dutch providers are no longer required to retain internet and phone traffic data. The telecommunications data retention law, that was fought in court by various privacy groups and small ISPs, is invalid.
That was ruled by the court of The Hague on Wednesday. The data retention law violated the Charter of Fundamental Rights of the European Union, specifically regarding the right to protection of private life and protection of personal data.
As that report from Nu.nl, translated by Matthijs R. Koot on his blog, makes clear, the court’s judgment affects all kinds of telecoms — both Internet and phone traffic data — and all communication providers. This is the judge’s reasoning:
The judge finds that the collected data are too easily accessible for crimes that are not serious. The plaintiffs stated that, technically, theft of a bicycle could lead to access to data, although the government stated this does not happen.
“Fact of the matter is that the possibility exists and that no safeguards exist to limit access to the data to what is strictly necessary to fight (only) serious crime”, according to the judge.
The court also finds it to be incorrect that no prior court approval is needed to access the data.
The judge’s ruling is only “provisonally enforeable”, and the Dutch government may appeal against it. But even if it does, it has a larger problem with its policy in this area. Although it claims a new data retention bill will be compatible with the CJEU ruling, the Netherlands’ Data Protection Authority has already said that it is still too intrusive for a number of reasons. Clearly, the European debate over what is a reasonable and proportionate level of data retention — if any — has a long way to go yet, both in the Netherlands and elsewhere.
Kaspersky claims to have found NSA’s ‘space station malware’
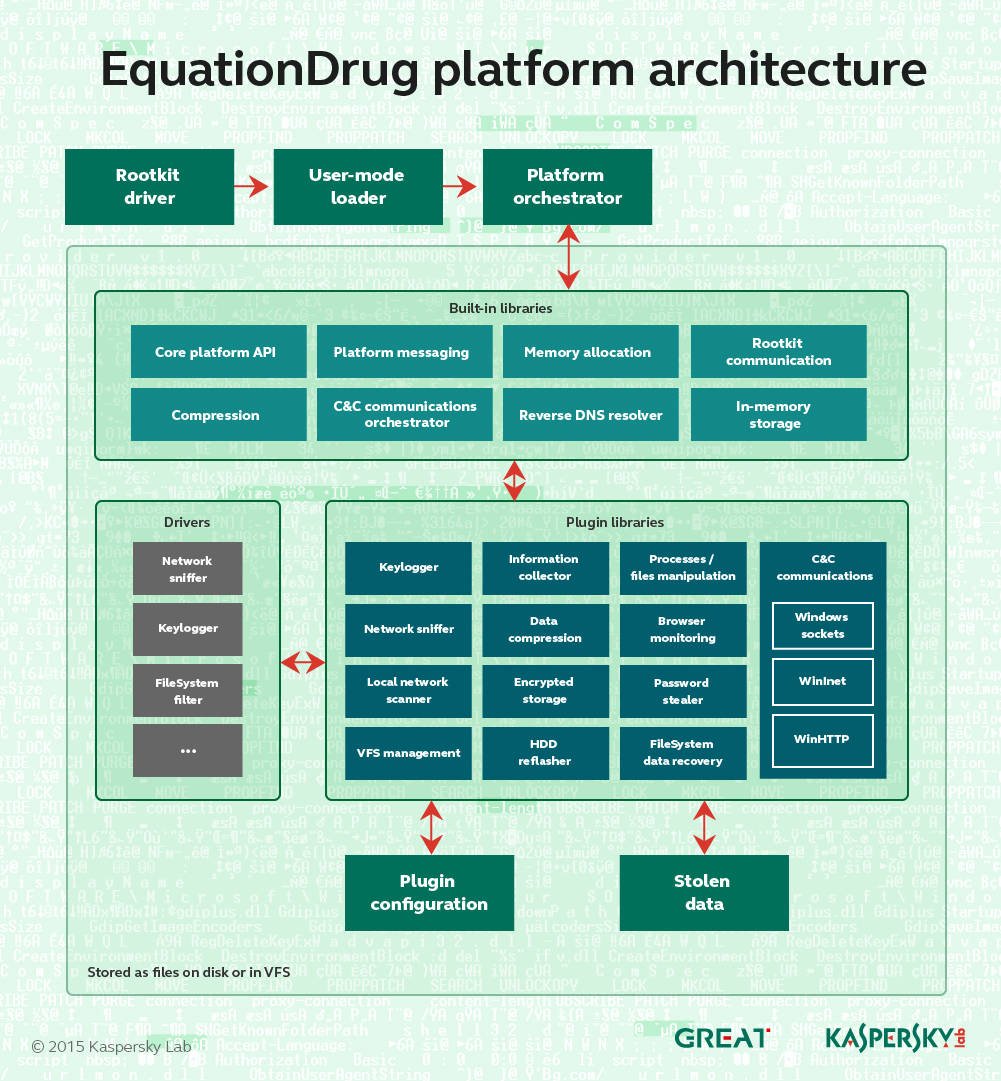
Kaspersky malware probers have uncovered a new ‘operating system’-like platform they was developed and used by the National Security Agency (NSA) in its Equation spying arsenal.
The EquationDrug or Equestre platform is used to deploy 116 modules to target computers that can siphon data and spy on victims.
“It’s important to note that EquationDrug is not just a trojan, but a full espionage platform, which includes a framework for conducting cyberespionage activities by deploying specific modules on the machines of selected victims,” Kaspersky researchers say in a report.
“Other threat actors known to use such sophisticated platforms include Regin and Epic Turla.
“The architecture of the whole framework resembles a mini-operating system with kernel-mode and user-mode components carefully interacting with each other via a custom message-passing interface.”
The platform is part of the NSA’s possibly ongoing campaign to infect hard disk firmware. It replaces the older EquationLaser and is itself superseded by the GrayFish platform.
Kaspersky says the newly-identified wares are as “sophisticated as a space station” thanks to the sheer number of included espionage tools.
Extra modules can be added through a custom encrypted file system containing dozens of executables that together baffle most security bods.
Most of the unique identifiers and codenames tied to modules is encrypted and obfuscated. Some modules capabilities can be determined with unique identification numbers. Others are dependent on other plugins to function.
Each plugin has a unique ID and version number that defines a set of functions it can provide. Some of the plugins depend on others and might not work unless dependencies are resolved.
Kaspersky bods have found 30 of the 116 modules estimated to exist.
“The plugins we discovered probably represent just a fraction of the attackers’ potential,” the researchers say.
Executable timestamps reveal NSA developers likely work hardest on the platform on Tuesdays to Fridays, perhaps having late starts to Monday.
Modules detected in the tool include code for:
- Network traffic interception for stealing or re-routing
- Reverse DNS resolution (DNS PTR records)
- Computer management
- Start/stop processes
- Load drivers and libraries
- Manage files and directories
- System information gathering
- OS version detection
- Computer name detection
- User name detection
- Locale detection
- Keyboard layout detection
- Timezone detection
- Process list
- Browsing network resources and enumerating and accessing shares
- WMI information gathering
- Collection of cached passwords
- Enumeration of processes and other system objects
- Monitoring LIVE user activity in web browsers
- Low-level NTFS filesystem access based on the popular Sleuthkit framework
- Monitoring removable storage drives
- Passive network backdoor (runs Equation shellcode from raw traffic)
- HDD and SSD firmware manipulation
- Keylogging and clipboard monitoring
- Browser history, cached passwords and form auto-fill data collection.
AT&T’s Cozy NSA Ties Brought Up In Attempt To Scuttle DirecTV Merger
Before there was Edward Snowden, there was of course the notably less celebrated Mark Klein. As most of you probably recall, Klein, a 22-year AT&T employee, became a whistleblower after hehighlighted how AT&T was effectively using fiber splits to give the NSA duplicate access to every shred of data that touched AT&T’s network. Of course, once it was discovered that AT&T was breaking the law, the government decided to just change the law, ignore Klein’s testimony, and give all phone companies retroactive immunity. It really wasn’t until Snowden that the majority of the tech press took Klein’s warnings seriously.
AT&T’s been loyally “patriotic” ever since, often giving the government advice on how to skirt the lawor at times even acting as intelligence analysts. Business repercussions for AT&T have been minimal at best; in fact, you’ll recall that Qwest (now CenturyLink) claimed repeatedly that government cooperation was rewarded with lucrative contracts, while refusal to participate in government programs was punished. In fact, the only snag AT&T’s seen in the years since was to have its European expansion plans thwarted, purportedly by regulators uncomfortable with the carrier’s cozy NSA ties (AT&T instead simply expanded into Mexico).
Fast forward a few years and The Hill is now claiming that AT&T’s relationship with the NSA could harm the company’s $48 billion attempt to acquire DirecTV. This claim is apparently based on the fact that a coalition of AT&T business partners, called the Minority Cellular Partners Coalition, is warning the FCC in a letter that AT&T’s enthusiastic voluntary cooperation with the NSA shows the company’s total disregard for consumer privacy.
“(Despite immunity) the Commission is still obliged to execute and enforce the provisions of § 229 of the Act, see 47 U.S.C. § 151, and it is still empowered to conduct an investigation to insure that AT&T complies with the requirements of CALEA. See id. § 229(c). And the Commission is obliged to determine whether AT&T is qualified to obtain DIRECTV’s licenses in light of its egregious violations of CALEA. This is particularly true given AT&T’s continued and ongoing pattern of misconduct. Accordingly, the Commission should investigate AT&T’s complicity in the PSP to determine whether AT&T engaged in unlawful conduct that abridged the privacy interests of telecommunications consumers on a vast scale and, if so, whether AT&T is qualified to obtain DIRECTV’s licenses.”
Of course, that’s simply not happening. While the NSA cooperation can be used as a broader example of AT&T’s character (like the repeatedly nonsensical claims the company makes when it wants a merger approved, or how AT&T tries to charge its broadband customers extra for no deep packet inspection), it’s incredibly unlikely that the same government that granted AT&T’s immunity will turn around and sign off on using AT&T’s behavior to squash a merger. If the merger is blocked, it will be due to more practical considerations — like the fact that DirecTV is a direct competitor to AT&T and eliminating them would lessen competition in the pay TV space. When it comes to AT&T’s relationship with the NSA, it’s pretty clear by now that these particular chickens may never come home to roost.
Che Vergogna
Italy does not exactly have the greatest track record of being nice to Ethiopians. Things haven’t changed, as an Italian group is helping the Ethiopian government spy on uncooperative journalists.
The CIA Campaign to Steal Apple’s Secrets
RESEARCHERS WORKING with the Central Intelligence Agency have conducted a multi-year, sustained effort to break the security of Apple’s iPhones and iPads, according to top-secret documents obtained by The Intercept.
The security researchers presented their latest tactics and achievements at a secret annual gathering, called the “Jamboree,” where attendees discussed strategies for exploiting security flaws in household and commercial electronics. The conferences have spanned nearly a decade, with the first CIA-sponsored meeting taking place a year before the first iPhone was released.
By targeting essential security keys used to encrypt data stored on Apple’s devices, the researchers have sought to thwart the company’s attempts to provide mobile security to hundreds of millions of Apple customers across the globe. Studying both “physical” and “non-invasive” techniques, U.S. government-sponsored research has been aimed at discovering ways to decrypt and ultimately penetrate Apple’s encrypted firmware. This could enable spies to plant malicious code on Apple devices and seek out potential vulnerabilities in other parts of the iPhone and iPad currently masked by encryption.
The CIA declined to comment for this story.
The security researchers also claimed they had created a modified version of Apple’s proprietary software development tool, Xcode, which could sneak surveillance backdoors into any apps or programs created using the tool. Xcode, which is distributed by Apple to hundreds of thousands of developers, is used to create apps that are sold through Apple’s App Store.
The modified version of Xcode, the researchers claimed, could enable spies to steal passwords and grab messages on infected devices. Researchers also claimed the modified Xcode could “force all iOS applications to send embedded data to a listening post.” It remains unclear how intelligence agencies would get developers to use the poisoned version of Xcode.
Researchers also claimed they had successfully modified the OS X updater, a program used to deliver updates to laptop and desktop computers, to install a “keylogger.”
Australian Government Prosecuting Anonymous Member Who Allegedly Exposed The Major Flaw In Its Data Retention Demands
Find a security flaw, go to jail. That’s the general attitude of government entities around the world. Over in Australia, an Anonymous member and fundraising manager for a cancer support group is facing an ever-shifting number of charges for finding and testing security holes.
Adam John Bennett is a rather un-anonymous member of Anonymous. He also acts as an unofficial mouthpiece for Anonymous via his LoraxLive online radio show. His supposed participation in a large-scale hack saw him raided by Australian Federal Police in May of 2014. Since then, he’s been awaiting prosecution for a variety of charges — charges government prosecutors seem unable to pin down.
The data breach leading to Bennett’s arrest involved a target of Australia’s controversial data retention law, which requires ISPs to hold onto subscribers’ internet activity (including social network use and emails) for two years and grant extensive access to a variety of government agencies.
New Zealand Prime Minister Retracts Vow To Resign if Mass Surveillance Is Shown
In August, 2013, as evidence emerged of the active participation by New Zealand in the “Five Eyes” mass surveillance program exposed by Edward Snowden, the country’s conservative Prime Minister, John Key, vehemently denied that his government engages in such spying. He went beyond mere denials, expressly vowing to resign if it were ever proven that his government engages in mass surveillance of New Zealanders. He issued that denial, and the accompanying resignation vow, in order to re-assure the country over fears provoked by a new bill he advocated to increase the surveillance powers of that country’s spying agency, Government Communications Security Bureau (GCSB) – a bill that passed by one vote thanks to the Prime Minister’s guarantees that the new law would not permit mass surveillance.
Since then, a mountain of evidence has been presented that indisputably proves that New Zealand does exactly that which Prime Minister Key vehemently denied – exactly that which he said he would resign if it were proven was done. Last September, we reported on a secret program of mass surveillance at least partially implemented by the Key government that was designed to exploit the very law that Key was publicly insisting did not permit mass surveillance. At the time, Snowden, citing that report as well as his own personal knowledge of GCSB’s participation in the mass surveillance tool XKEYSCORE, wrote in an article for the Intercept:
Let me be clear: any statement that mass surveillance is not performed in New Zealand, or that the internet communications are not comprehensively intercepted and monitored, or that this is not intentionally and actively abetted by the GCSB, is categorically false. . . . The prime minister’s claimto the public, that “there is no and there never has been any mass surveillance” is false. The GCSB, whose operations he is responsible for, is directly involved in the untargeted, bulk interception and algorithmic analysis of private communications sent via internet, satellite, radio, and phone networks.
Aussie Anti-Piracy Plans Boost Demand for Anonymous VPNs
Australia has been called out as the world’s piracy capital for several years, a claim that eventually captured the attention of the local Government.
After negotiations between ISPs and entertainment companies bore no fruit, authorities demanded voluntary anti-piracy measures from Internet providers. If that failed, the Government threatened to tighten the law.
Faced with an ultimatum the telecoms body Communications Alliance published a draft proposal on behalf of the ISPs, outlining a three-strikes notification system.
Titled ‘Copyright Notice Scheme Industry Code‘, the proposal suggests that ISPs start to forward infringement notices to their subscribers. After the initial notice subscribers are warned that copyright holders may go to court to obtain their identities.
Several groups have voiced their concerns in response. Australia’s leading consumer group Choice, for example, warns over the potential for lawsuits and potentially limitless fines.
These threats haven’t gone unnoticed by the general public either. While the proposals have not yet been implemented, many Australians are already taking countermeasures.
Over the past two weeks many file-sharers have been seeking tools to hide their IP-addresses and bypass the proposed monitoring system. By using VPN services or BitTorrent proxies their sharing activities can no longer be linked to their ISP account, rendering the three-strikes system useless.
Data from Google trends reveals that interest in anonymizing services has surged, with searches for “VPN” nearly doubling in recent days. This effect, shown in the graph below, is limited to Australia and appears to be a direct result of the ISPs proposals.