In rare remarks about a sensitive issue, the director of the CIA confirmed today that the U.S. government works with foreign intelligence agencies to capture and jointly interrogate suspected terrorists.
“There are places throughout the world where CIA has worked with other intelligence services and has been able to bring people into custody and engage in the debriefings of these individuals … through our liaison partners, and sometimes there are joint debriefings that take place as well,” said John Brennan, the CIA director, speaking at the Council on Foreign Relations in New York.
Brennan’s remarks confirm what journalists have long reported: that the Obama administration sometimes helps other countries do the dirty work of snatching and interrogating terror suspects — keeping the U.S. at arm’s length from operations that are ethically and legally dubious.
During a question-and-answer session, it was Fox News’ Megyn Kelley who questioned Brennan about “capturing terrorists.”
“Are we still doing that?” she asked. “And where are we keeping them and how are we interrogating them?”
Brennan responded that the U.S. is able to work with “partners” to “identify individuals and to have them captured … although there are not a lot of public pieces on Fox News about somebody that might be picked up in different parts of the world.”
In one of his first moves after taking office in 2009, President Obama famously shut down the CIA’s Black Site program, which was begun under President George W. Bush. After 9/11, more than 100 alleged terrorists were captured and sent to secret CIA-run detention centers where they were tortured and interrogated by agency operatives.
Although the Black Sites have been shut down and no new prisoners sent to Guantánamo Bay, detentions of terrorists — and attacks against them — remain a murky issue. The administration has brought several alleged terrorists to face trial in the United States, and it has killed thousands more in drone strikes, along with hundreds of civilians. Obama has also maintained the authority (as President Bill Clinton did in the 1990s) to render people to third countries, where laws are looser.
The Intercept’s Jeremy Scahill and others have detailed cases during the Obama administration in which terror suspects were held in foreign custody at the behest of the U.S. In 2011, Scahill reported for The Nation on a secret prison in Somalia’s capital, Mogadishu. Though officially run by the Somali government, Scahill wrote, “US intelligence personnel pay the salaries of intelligence agents and also directly interrogate prisoners” at the facility.
Tag: USA
Officials Upset Tech Companies Reluctant To Play Along With Administration’s ‘Information Sharing’ Charade
The government’s on-again, off-again love affair with everything cyber is back on again. The CIA has just shifted its focus, abandoning its position as the free world’s foremost franchiser ofclandestine torture sites and rebranding as the agency of choice for all things cyberwar-related.
For years, legislators have been attempting to grant themselves permission to strong-arm tech companies into handing over all sorts of information to the government under the guise of cybersecurity. CISPA, CISA, etc. The acronyms come and go, but the focus is the same: information sharing.
Of course, the promise of equitable sharing remains pure bullshit. Tech companies know this and have been understandably resistant to the government’s advances. There are few, if any positives, to these proposed “agreements.” The government gets what it wants — lots and lots of data — and the companies get little more than red tape, additional restrictions and fleeing customers.
The government has recently been playing up the narrative that unreasonable tech companies are standing in the way of the nation’s super-secure future.
U.S. government officials say privately they are frustrated that Silicon Valley technology firms are not obtaining U.S. security clearances for enough of their top executives, according to interviews with officials and executives in Washington and California. Those clearances would allow the government to talk freely with executives in a timely manner about intelligence they receive, hopefully helping to thwart the spread of a hack, or other security issues.
The lack of cooperation from Silicon Valley, Washington officials complain, injects friction into a process that everyone agrees is central to the fight to protect critical U.S. cyberinfrastructure: Real-time threat information sharing between government and the private sector.
Before dealing with the questionable promise of “real-time threat information sharing,” let’s deal with the supposedly minor requirement of security clearances. It’s not as if this won’t impose undue burdens on tech company leaders, especially when they already have a pretty good idea this stipulation will be a major hassle followed by continued opacity from a government that’s 90% lip service and 10% outright lying. Tech execs are being asked to make all the effort and hope against hope there will actually be some benefits.
“I believe that this is more about the overclassification of information and the relatively low value that government cyberintel has for tech firms,” said one Silicon Valley executive. “Clearances are a pain to get, despite what government people think. Filling out the paper work … is a nightmare, and the investigation takes a ridiculous amount of time.”
[…]
“I think tech companies are doing a return-on-investment analysis and don’t think the government intel is worth the cost or effort,” said the Silicon Valley executive. “This is why government threat signature sharing initiatives are such a nothing-burger: The signatures are of limited value and only a few select companies with clearances can actually use them.”
The clearance process can easily take over a year. The application runs 127 pages and asks a mixture of questions ranging from highly-intrusive to facially-ridiculous.
Ron Wyden: ‘Plenty’ Of Domestic Surveillance Programs Still Unexposed
In a few months, we’ll be marking the second anniversary of the first Snowden leak. The outraged responses of citizens and politicians around the world to these revelations has resulted in approximately nothing in those 24 months. There have been bright spots here and there — where governments and their intelligence agencies were painted into corners by multiple leaks and forced to respond — but overall, the supposed debate on the balance between security and privacy has been largely ignored by those on Team National Security.
Here in the US, multiple surveillance reforms were promised. So far, very little has been put into practice. The NSA may be forced to seek court approval for searches of its bulk phone metadata, but otherwise the program rolls on unimpaired and slightly rebranded (from Section 215 to Section 501).
Senator Ron Wyden — one of the few members of our nation’s intelligence oversight committees actively performing any oversight — isn’t happy with the lack of progress. In an interview with Buzzfeed’s John Stanton, Wyden points out that not only has there been little movement forward in terms of surveillance reform, there actually may have been a few steps backward.
Wyden bluntly warned that even after the NSA scandal that started with Edward Snowden’s disclosures, the Obama administration has continued programs to monitor the activities of American citizens in ways that the public is unaware of and that could be giving government officials intimate details of citizens’ lives.
Asked if intelligence agencies have domestic surveillance programs of which the public is still unaware, Wyden said simply, “Yeah, there’s plenty of stuff.
The Orwellian Re-Branding of “Mass Surveillance” as Merely “Bulk Collection”
Just as the Bush administration and the U.S. media re-labelled “torture” with the Orwellian euphemism “enhanced interrogation techniques” to make it more palatable, the governments and media of the Five Eyes surveillance alliance are now attempting to re-brand “mass surveillance” as “bulk collection” in order to make it less menacing (and less illegal). In the past several weeks, this is the clearly coordinated theme that has arisen in the U.S., U.K., Canada, Australia and New Zealand as the last defense against the Snowden revelations, as those governments seek to further enhance their surveillance and detention powers under the guise of terrorism.
This manipulative language distortion can be seen perfectly in yesterday’s white-washing report of GCHQ mass surveillance from the servile rubber-stamp calling itself “The Intelligence and Security Committee of the UK Parliament (ISC)”(see this great Guardian editorial this morning on what a “slumbering” joke that “oversight” body is). As Committee Member MP Hazel Blears explained yesterday (photo above), the Parliamentary Committee officially invoked this euphemism to justify the collection of billions of electronic communications events every day.
The Committee actually acknowledged for the first time (which Snowden documents long ago proved) that GCHQ maintains what it calls “Bulk Personal Datasets” that contain “millions of records,” and even said about pro-privacy witnesses who testified before it: “we recognise their concerns as to the intrusive nature of bulk collection.” That is the very definition of “mass surveillance,” yet the Committee simply re-labelled it “bulk collection,” purported to distinguish it from “mass surveillance,” and thus insist that it was all perfectly legal.
UN Cultural Rights Rapporteur Delivers Report Condemning Prevailing Copyright Laws
Shaheed said a “widely shared concern stems from the tendency for copyright protection to be strengthened with little consideration to human rights issues.” This is illustrated by trade negotiations conducted in secrecy, and with the participation of corporate entities, she said.
She stressed the fact that one of the key points of her report is that intellectual property rights are not human rights. “This equation is false and misleading,” she said.
Project G650
This story has gone viral on twitter this morning for all the wrong reasons. Celebrity pastor Creflo Dollar, worth a reported 27 million dollars, is crowdfunding a new private jet worth a reported 65 million dollars. Dubbed Project G650, the pastor is requesting his followers donate to the project “in order to continue to spread the word of god across the globe”.
The mission of Project G650 is to acquire a Gulfstream G650 airplane so that Pastors Creflo and [wife] Taffi and World Changers Church International can continue to blanket the globe with the Gospel of grace. … We are believing for 200,000 people to give contributions of 300 US dollars or more to make this a reality—and allow us to retire the aircraft that served us well for many years.
This isn’t really that shocking as I assume stuff like this happens all the time. Its the nature of the (celebrity evangelical megachurch) business. Still, 65 million dollars could feed a lot of folks, or put shoes on their feet.
Angry Austrian could turn Europe against the US – thanks to data
In a David versus Goliath battle, an Austrian law student may topple the biggest EU-US data sharing deal when he gets his day in court in a couple of weeks’ time.
Max Schrems, who set up the Europe v Facebook group, alleges that Facebook violated the so-called safe harbour agreement which protects EU citizens’ privacy by transferring personal user data to the US National Security Agency (NSA).
The European Court of Justice (ECJ) will hear details of the case on 24 March.
Schrems first appealed to the Irish Data Protection Commissioner to investigate his claims. He was refused on the grounds that Facebook was signed up to the safe harbour agreement and so could transfer data to the US with impunity.
Under European data protection law, companies can only transfer consumer data out of the EU to countries where there is an “adequate” level of privacy protection. As the US does not meet this adequacy standard, the European Commission and the US authorities came up with a workaround and, in 2000, set up the voluntary safe harbour framework whereby companies promise to protect European citizens’ data.
These promises are enforced by the US Federal Trade Commission – but since the Snowden revelations, there has been doubt these promises are worth the paper they’re written on.
Mega Ponders Legal Action in Response to Damaging Paypal Ban
September last year the Digital Citizens Alliance and NetNames released a report that looked into the business models of “shadowy” file-storage sites.
Titled “Behind The Cyberlocker Door: A Report How Shadowy Cyberlockers Use Credit Card Companies to Make Millions,” the report offers insight into the money streams that end up at these alleged pirate sites.
The research claims that the sites in question are mostly used for copyright infringement. But while there are indeed many shadowy hosting services, many were surprised to see the Kim Dotcom-founded Mega.co.nz on there.
For entertainment industry groups the report offered an opportunity to put pressure on Visa and MasterCard. In doing so they received support from U.S. Senator Patrick Leahy, who was also the lead sponsor of the defunct controversial Protect IP Act (PIPA).
Senator Leahy wrote a letter to the credit card companies claiming that the sites mentioned in the report have “no legitimate purpose or activity,” hoping they would cut their connections to the mentioned sites.
Visa and MasterCard took these concerns to heart and pressed PayPal to cut off its services to Mega, which eventually happened late last month. Interestingly, PayPal cited Mega’s end-to-end-encryption as one of the key problems, as that would make it harder to see what files users store.
The PayPal ban has been a huge blow for Mega, both reputation-wise and financially. And the realization that the controversial NetNames report is one of the main facilitators of the problems is all the more frustrating.
TorrentFreak spoke with CEO Graham Gaylard, who previously characterized the report as “grossly untrue and highly defamatory,” to discuss whether Mega still intends to take steps against the UK-based NetNames for their accusations.
Initially, taking legal action against NetNames for defamation was difficult, as UK law requires the complaining party to show economic damage. However, after the PayPal ban this shouldn’t be hard to do.
Gaylard is traveling through Europe at the moment and he notes that possible repercussions against the damaging report are high on the agenda.
“Yes, I am here to see Mega’s London-based legal counsel to discuss the next steps in progressing the NetNames’ response,” Gaylard informs TF.
Mega’s CEO couldn’t release any details on a possible defamation lawsuit, but he stressed that his company will fiercely defend itself against smear campaigns.
“Mega has been operating, and continues to operate a completely legitimate and transparent business. Unfortunately now, with the blatant, obvious, political pressure and industry lobbying against Mega, Mega needs to defend itself and will now cease taking a passive stance,” Gaylard says.
According to the CEO Mega is running a perfectly legal business. The allegation that it’s a piracy haven is completely fabricated. Like any other storage provider, there is copyrighted content on Mega’s servers, but that’s a tiny fraction of the total stored.
To illustrate this, Gaylard mentions that they only receive a few hundred takedown notices per month. In addition, he notes more than 99.7% of the 18 million files that are uploaded per day are smaller than 20MB in size, not enough to share a movie or TV-show.
These statistics are certainly not the hallmark of a service with “no legitimate purpose or activity,” as was claimed.
While the PayPal ban is a major setback, Mega is still doing well in terms of growth. They have 15 million registered customers across 200 countries, and hundreds of thousands of new users join every month.
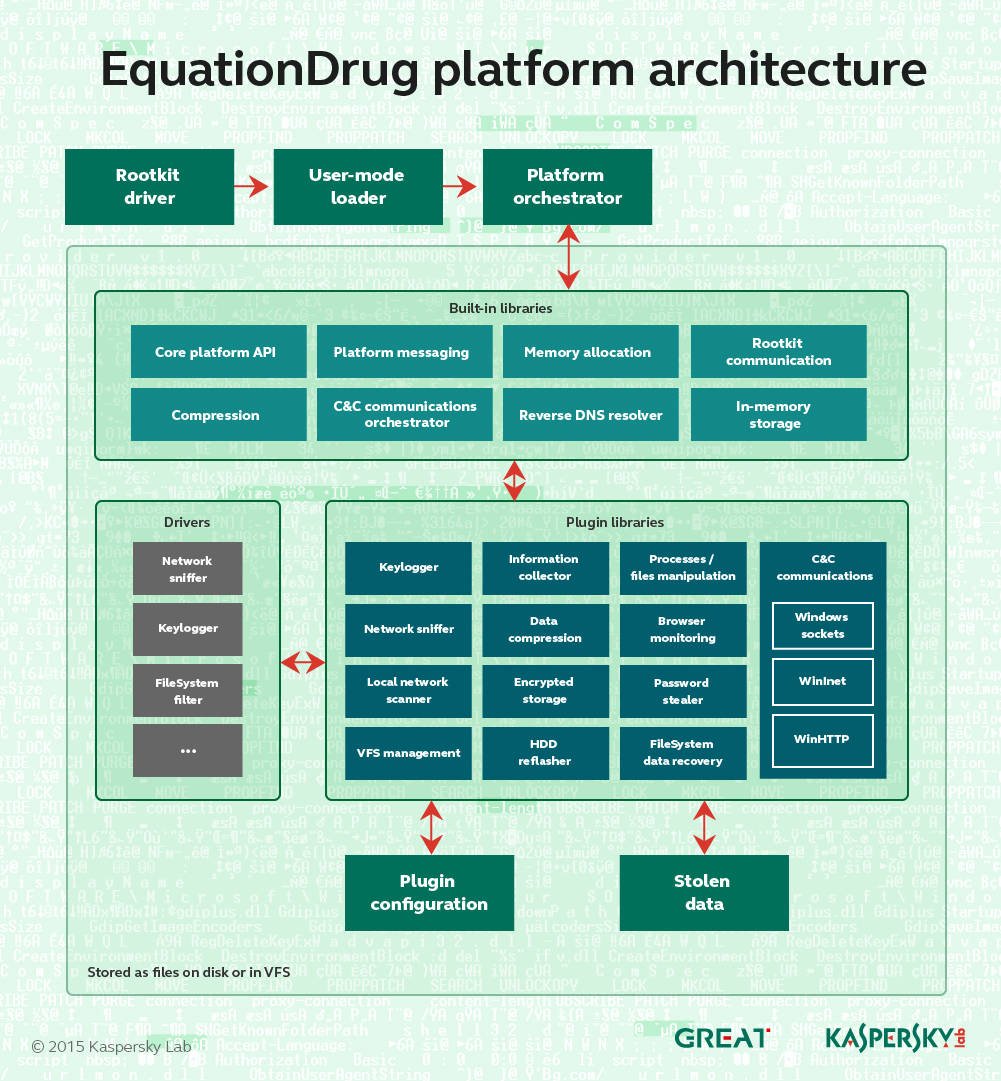
Kaspersky claims to have found NSA’s ‘space station malware’
Kaspersky malware probers have uncovered a new ‘operating system’-like platform they was developed and used by the National Security Agency (NSA) in its Equation spying arsenal.
The EquationDrug or Equestre platform is used to deploy 116 modules to target computers that can siphon data and spy on victims.
“It’s important to note that EquationDrug is not just a trojan, but a full espionage platform, which includes a framework for conducting cyberespionage activities by deploying specific modules on the machines of selected victims,” Kaspersky researchers say in a report.
“Other threat actors known to use such sophisticated platforms include Regin and Epic Turla.
“The architecture of the whole framework resembles a mini-operating system with kernel-mode and user-mode components carefully interacting with each other via a custom message-passing interface.”
The platform is part of the NSA’s possibly ongoing campaign to infect hard disk firmware. It replaces the older EquationLaser and is itself superseded by the GrayFish platform.
Kaspersky says the newly-identified wares are as “sophisticated as a space station” thanks to the sheer number of included espionage tools.
Extra modules can be added through a custom encrypted file system containing dozens of executables that together baffle most security bods.
Most of the unique identifiers and codenames tied to modules is encrypted and obfuscated. Some modules capabilities can be determined with unique identification numbers. Others are dependent on other plugins to function.
Each plugin has a unique ID and version number that defines a set of functions it can provide. Some of the plugins depend on others and might not work unless dependencies are resolved.
Kaspersky bods have found 30 of the 116 modules estimated to exist.
“The plugins we discovered probably represent just a fraction of the attackers’ potential,” the researchers say.
Executable timestamps reveal NSA developers likely work hardest on the platform on Tuesdays to Fridays, perhaps having late starts to Monday.
Modules detected in the tool include code for:
- Network traffic interception for stealing or re-routing
- Reverse DNS resolution (DNS PTR records)
- Computer management
- Start/stop processes
- Load drivers and libraries
- Manage files and directories
- System information gathering
- OS version detection
- Computer name detection
- User name detection
- Locale detection
- Keyboard layout detection
- Timezone detection
- Process list
- Browsing network resources and enumerating and accessing shares
- WMI information gathering
- Collection of cached passwords
- Enumeration of processes and other system objects
- Monitoring LIVE user activity in web browsers
- Low-level NTFS filesystem access based on the popular Sleuthkit framework
- Monitoring removable storage drives
- Passive network backdoor (runs Equation shellcode from raw traffic)
- HDD and SSD firmware manipulation
- Keylogging and clipboard monitoring
- Browser history, cached passwords and form auto-fill data collection.
Walmart Not Horsing Around With Parody Domain Site
Another strike for the Streisand Effect
Walmart. Just saying the company’s name is usually enough to evoke unbidden brain-sounds of terrifying organ music and images of pitchfork-wielding devil-imps. But, hey, it’s a large business that’s been around for quite a while, so I guess it’s doing alright. It seems to me that somebody might want to call a meeting with the Walmart legal brain trust, because the company’s campaign against a silly and simple parody website isn’t achieving much of anything at all, and is in fact Streisanding the parody site into national views.
This story starts back in 2012, when ICANN saw fit to hold a firesale on domain extensions. Buying them up was all the rage for reasons unfathomable to this author. Still, that was the impetus for how we arrived at Walmart going after a site with a .horse extension.
That explains why, for the mere price of $29, you can now purchase a .horse domain name, if you want to do such a thing. “With .HORSE, there are no hurdles between equine enthusiasts on the Internet,” says United Domains. “Giddy up and register .HORSE today!” It doesn’t seem like too many people have been receptive to this pun-based sales pitch, but a 34-year-old named Jeph Jacques saw the opportunity for what he calls an “art project.”
“I thought, ‘Alright I’m gonna buy this and do something stupid with it and see what happens,” he told me. And readers, he did just that.
This grand art project? Buying up the domain www.walmart.horse, slapping a picture of the front of a Walmart store with a, you guessed it, horse superimposed over the top, and declaring the whole thing a monumental artistic success. Seriously, this is the only thing at the website if you go there.
Monet it might not be, but the image is suddenly competing with the likes of famous artists for attention and views thanks to Walmart freaking the hell out about it. In its infamous wisdom, Walmart and its crackerjack legal team have demanded that the whole shebang be taken down, claiming infringement of trademark. The C&D letter Walmart helpfully sent along suggested that Jacques’ website would confuse customers into thinking that Walmart, who is not in either the business of horses nor in the business of having a sense of humor, might have some affiliation to walmart.horse. Interestingly, the letter targets the domain name, rather than the image on the site itself. I’m not personally aware of any infringement claim on domain name being refuted by the actual extension used, but this would seem to be a ripe candidate for that argument, given that Walmart is not in the horse business.
But this really shouldn’t even get that far, given the whole purpose of the site itself and the artistic nature of the creator.
Jacques argues that his site is “an obvious parody and therefore falls under fair use.” He also told Walmart in his response that he’d be happy to put a disclaimer on his site to let visitors know he is not actually affiliated with the Waltons. And although he doesn’t want to bow to the company just yet, he says he’s already proved his original hypothesis: that corporations spend an absurd amount of time policing their trademarks.
Point proven, I suppose. Meanwhile, a tiny joke site has been Streisanded into the national conversation because Walmart just couldn’t resist.
![This story has gone viral on twitter this morning for all the wrong reasons. Celebrity pastor Creflo Dollar, worth a reported 27 million dollars, is crowdfunding a new private jet worth a reported 65 million dollars. Dubbed Project G650, the pastor is requesting his followers donate to the project “in order to continue to spread the word of god across the globe”. The mission of Project G650 is to acquire a Gulfstream G650 airplane so that Pastors Creflo and [wife] Taffi and World Changers Church International can continue to blanket the globe with the Gospel of grace. … We are believing for 200,000 people to give contributions of 300 US dollars or more to make this a reality—and allow us to retire the aircraft that served us well for many years.This isn’t really that shocking as I assume stuff like this happens all the time. Its the nature of the (celebrity evangelical megachurch) business. Still, 65 million dollars could feed a lot of folks, or put shoes on their feet.](http://40.media.tumblr.com/61d41fe5e40d9fe4264376aaa0d15be6/tumblr_nl5qfiCuQs1rugltbo1_1280.jpg)