I recommend that everyone watches this keynote by Matthew Inman
Month: December 2014
FastType
The QWERTY keyboard layout was invented 140 years ago to prevent traditional type writers from tangling up.
However, that doesn’t mean it can’t be improved upon, and FastType looks like a neat idea.
OPERATION AURORAGOLD HOW THE NSA HACKS CELLPHONE NETWORKS WORLDWIDE
In March 2011, two weeks before the Western intervention in Libya, a secret message was delivered to the National Security Agency. An intelligence unit within the U.S. military’s Africa Command needed help to hack into Libya’s cellphone networks and monitor text messages.
For the NSA, the task was easy. The agency had already obtained technical information about the cellphone carriers’ internal systems by spying on documents sent among company employees, and these details would provide the perfect blueprint to help the military break into the networks.
The NSA’s assistance in the Libya operation, however, was not an isolated case. It was part of a much larger surveillance program—global in its scope and ramifications—targeted not just at hostile countries.
According to documents contained in the archive of material provided to The Intercept by whistleblower Edward Snowden, the NSA has spied on hundreds of companies and organizations internationally, including in countries closely allied to the United States, in an effort to find security weaknesses in cellphone technology that it can exploit for surveillance.
The documents also reveal how the NSA plans to secretly introduce new flaws into communication systems so that they can be tapped into—a controversial tactic that security experts say could be exposing the general population to criminal hackers.
Codenamed AURORAGOLD, the covert operation has monitored the content of messages sent and received by more than 1,200 email accounts associated with major cellphone network operators, intercepting confidential company planning papers that help the NSA hack into phone networks.
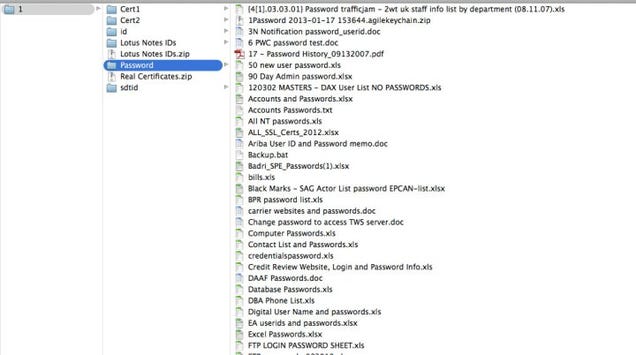
Sony Kept Thousands of Passwords in a Folder Named “Password”
It’s been a rough week for Sony execs (million-dollar salaries notwithstanding). And things are only going to get worse. Which would almost be enough to make you feel bad for the poor schmucks in IT—that is, until you realize that they hid their most sensitive password data under the label “Passwords.” Go ahead and slam your head against something hard. We’ll wait.
Defining The Patent Troll
Recently, the IP Troll Tracker blog decided to try to officially define “patent troll” to a level that might satisfy a patent holder who insists that there is no such thing as a patent troll. For many years, we here at Techdirt avoided using the phrase “patent troll” because it did seem rather undefined, but it became so commonplace that we eventually gave in and used the phrase regularly. The term has showed up in all sorts of places, including courtrooms and discussions on legislation. In some circles, policy makers often use the term “non-practicing entities” (or NPEs) instead of “patent trolls” but that upsets some who feel that there are “NPEs” (like universities) that do research that they wish to license off, but which will never be “practicing entities.” Some have also called them “Patent Assertion Entities” (PAEs) to describe companies who do nothing more than assert patents. At least that leaves out universities — but then that also leaves out companies who do other things but who also, do some patent trolling (including, frankly, some universities, since we’re discussing them).
Stephanie Kennedy, who runs the IP Troll Tracker blog, came up with the following definition:
Patent Troll, n –
1/ A company or individual who, using patents that either never should have been issued or are broadly constructed (intentionally for the purpose of misuse, or as a result of poor USPTO patent examination practices), sends letters to various and sundry companies and/or individuals that simultaneously request license fees and threaten legal action if the recipient fails to respond correctly by paying up and who will, in the face of inaction by a demand letter recipient, actually file suit in Federal District Court, the District of East Texas being the most popular venue.2/ A company set up to act as a cover for large corporations who try to breathe new life into older patents which they would ordinarily let expire but, as a result of greed and/or pressure from Wall Street, have decided are ripe for assertion or litigation.
3/ Intellectual Ventures